1-What is Penetration Testing?
A penetration test is an authorized simulated attack performed on a computer system to evaluate its security. Penetration testers use the same tools, techniques, and processes as attackers to find and demonstrate the business impacts of weaknesses in your systems.
Penetration tests usually simulate a variety of different attacks that could threaten your business. A pen test might examine whether a system is robust enough to resist attacks from authenticated and unauthenticated positions, as well as a range of system roles. With the right scope, a pen test can dive into any aspect of a system that you need to assess
Why Should an Organization or company Carry Out Penetration Testing? reasons to conduct pen testing:
To determine threats and weaknesses in the overall infrastructure, both hardware, and software, to develop a sound security control system.
To uncover gaps within the organization existing security posture and address them specifically and effectively.
To ensure that the security system or controls in place are effective and mitigate the risks of an attack.
To priorities attack vectors and secure attack avenues that are more prone to an attack.To discover existing bugs in the security control system and fix them.
To determine and detect the possible magnitude of the breach and to improve the overall security response time to an attack.
Here are common scenarios when you can consider pen testing:
To ensure the security of your company’s data
You can consider pen testing as a part of the development cycle of the web application
When you have to modify end-user policies
Establish a different branch of your office in a new location
To prevent cyber attack due to malware or any other means
When you need to make crucial upgrades in the applications or network infrastructure
You need pen testing to comply with security standards as discussed above
To ensure proper implementation of your cybersecurity risk management strategy
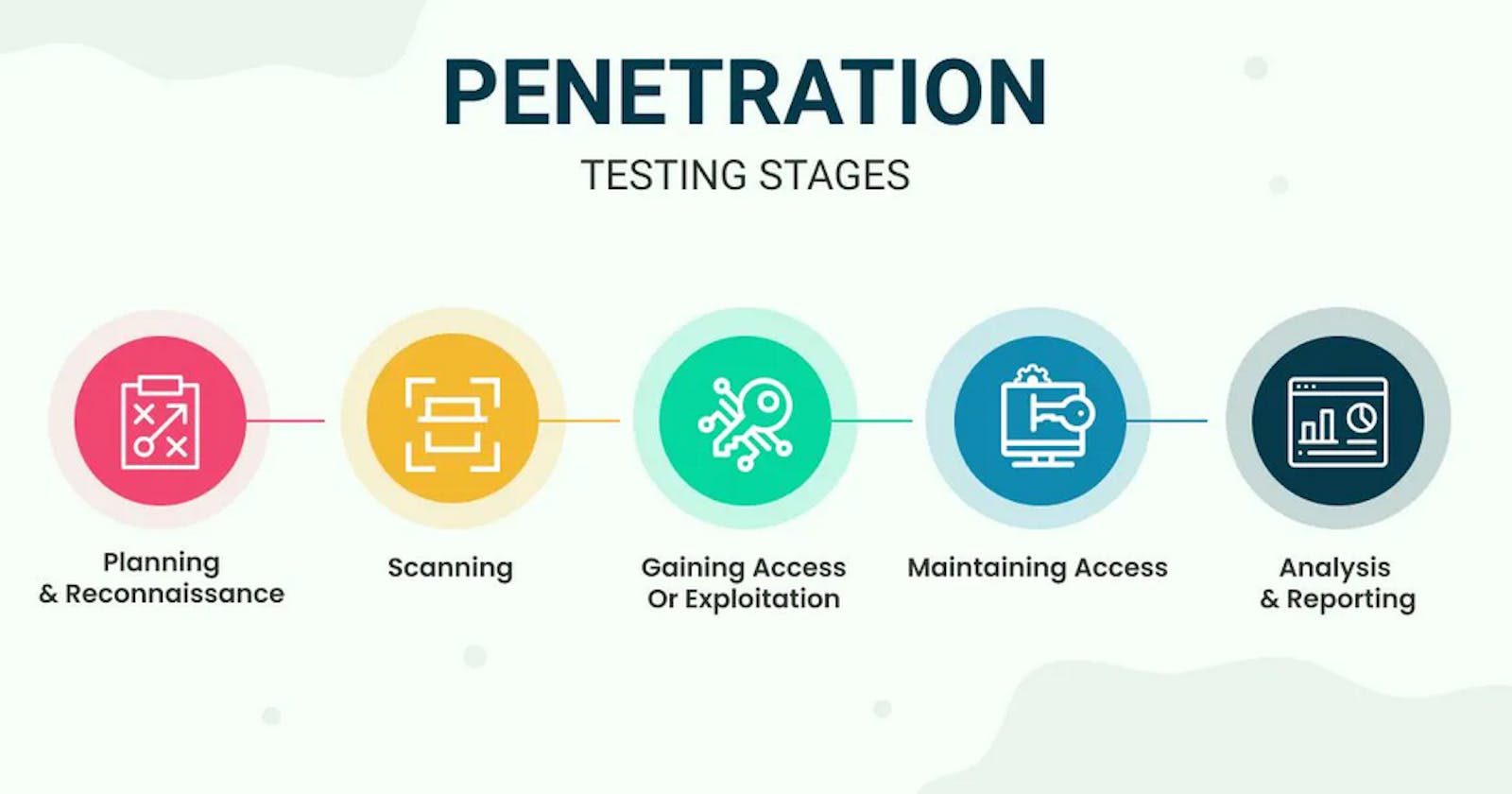
2-What are The Stages of Penetration Testing?
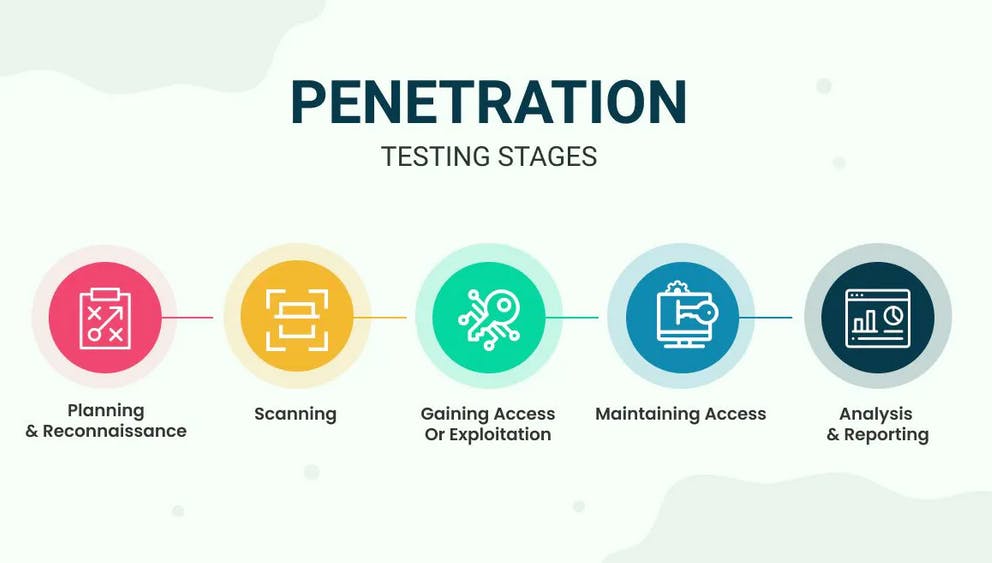
Penetration test involves simulated breaching of any number of applications or systems such as application protocol interfaces, front-end or back-end servers, security infrastructure, and unsensitised inputs to detect vulnerabilities and threats.
The pen testing process usually includes five stages and helps the organization to fine-tune their environment for fixing security loopholes.
The stages are as follows:
- Planning and Reconnaissance
This stage includes defining the scope, priorities, and goals to be achieved. It also states the primary critical systems to be tested or addressed and types of test to be performed.
The reconnaissance stage includes gathering intelligence like passive and active information on network and domain names or mail servers et al. of the target system to better understand how a target works and its potential entry points.
- Scanning
This stage involves understanding how the target system responds to various automated intrusion attempts and attacks. This is typically done using following.
Static Analysis – Inspects the application source code before a program is run by comparing it to a set of coding rules followed by debugging
Dynamic Analysis – is the testing and evaluation of the security system by executing data in real-time. The objective here is to find errors or vulnerabilities in real-time by scanning the application or systems using automated security scanning tools. Static or dynamic analysis is followed by manual verification of vulnerabilities or errors to eliminate false positives.
- Gaining Access or Exploitation
In this stage, the vulnerabilities identified are actively exploited to gain access to the system or valuable information.
The vulnerabilities can be exploited by escalating privileges, stealing data, intercepting traffic and injecting malicious code to understand or observe the magnitude of the damage caused.
- Maintaining Access
The objective of this stage is to check if persistence access can be maintained after gaining access to the application or its underlying system.
The longer the attacker maintains access to the system, the more in-depth access he/she gains. The goal is to imitate and detect advanced persistent threats that often remain in a system without being detected.
- Analysis and Reporting
The results of the test are then compiled into a detailed report. The report primarily contains vulnerabilities that were exploited, sensitive data that was breached and accessed, and the amount of time the security tester could remain in the system before getting detected.
-Methods of Penetration Testing
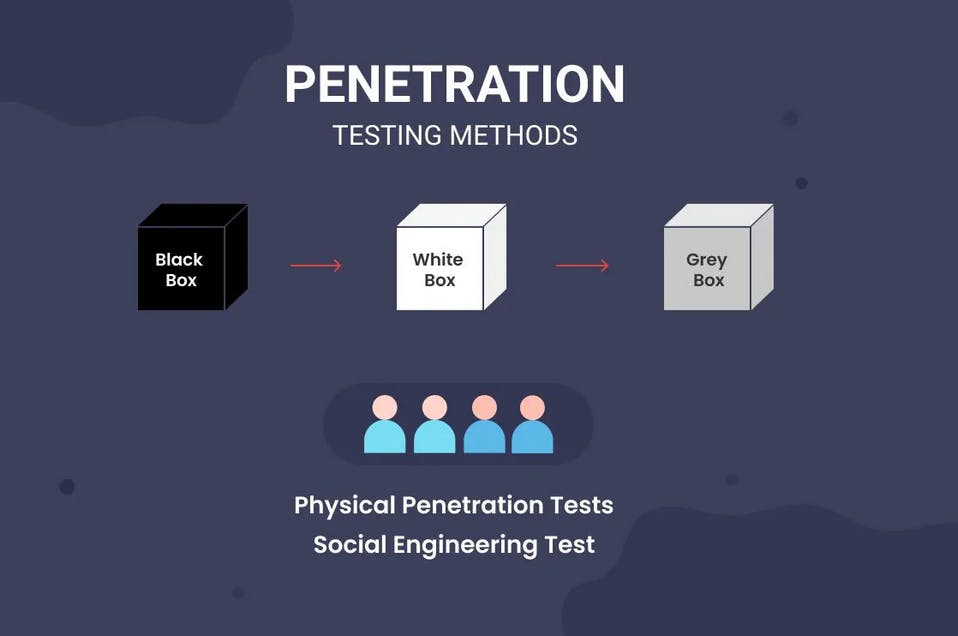
Many penetration testing methods are depending upon the security system and the level of motivation of the organisation. A security expert or a Cyber Security Firm should help you choose or determine a perfect match as per the organisation’s requirements.
The different types of pen testing methods are as follows. Depending upon the type of information a security expert or a pen tester has, the methods can be divided into:
Black Box
A black box assessment is carried out with little information provided to the pen tester. The security consultant or the tester will have very limited knowledge about the security control system or the infrastructure.
Typically, the consultant will undertake the reconnaissance methodology to gain information about the system and security infrastructure.
White Box
In the white box assessment, the tester or the consultant is provided with information and detailed documentation regarding the infrastructure, applications, equipment’s and security control system such as system architecture documents, source code and more.
It is a comprehensive assessment method to identify and detect external as well internal vulnerabilities.
Grey Box
In this assessment method, the tester is provided with user-level knowledge and information needed to assess the security control system. The testers are also granted limited access and partial knowledge to the web applications and the internal network infrastructure.
Physical Penetration Tests
The organisation should be wary of hackers adopting a physical approach to gain facility access either as a standalone attack or to complement their technical attacks.
The following are physical penetration tests:
Scoping Unsecured Areas: In this method, hackers’ scope or search areas or systems that are vulnerable and are more prone to a breach or an attack. This may include smoking areas, maintenance docks, and unguarded entrances with the least resistance and visibility to gain facility access.
Piggybacking: Piggybacking, tailgating or eavesdropping are some methods wherein a hacker closely follows the employees or maintenance workers that have access to the facility area.
Social Engineering Test
These tests verify the Human Network of an organization. This test helps determine and secure an attack from within an organization from the employee who is either initiating an attack or has his credentials or privileged access compromised.
The types of attacks are:
Phishing: A deceptive method wherein personal information is gained by sending across malicious or infected codes via mail or messages.
Pretesting: Pretesting is a form of identity theft wherein the hackers present themselves as someone else who is a part of an organization and gain access to the security infrastructure or sensitive data.
3-Types of Penetration Testing
- Network Penetration Testing
A network penetration test is the most common and in-demand pen test method, which helps detect and exploit vulnerabilities in the network system or infrastructure. There are three types of Network pen testing, external, internal, and wireless.
External Network Penetration Testing: The external network pen test helps you probe how robust your external network system responds to threats.
The common tests included in the External network pen test are Internet-based pen testing which identifies vulnerabilities and weaknesses within the system that are exposed to the internet.
This test generally targets network areas like Firewall configuration, firewall bypass, IPS deception and DNS level attacks.
Vulnerability scanning is a type of test or an automated process that utilities the shelf tools to scan and detect known vulnerabilities in your system.
A combination of automated and manual exploitation techniques is a process wherein the vulnerabilities after detection are targeted, and a variety of attacks are simulated against these weaknesses with an aim to completely take over the internet-facing systems.
Internal Network Pen Testing: This test includes identifying or detecting security network weaknesses within your internal systems or infrastructure. This test too includes vulnerability scanning and exploitation techniques to detect the vulnerabilities and then exploit them to see how the internal systems respond.
The internal network pen test fundamentally evaluates the potential of an exploit by an internal user or an unauthorized attack by an employee of the organization, such as potential unauthorized access and leak of personal credentials or information.
Wireless Penetration Testing: Wireless systems allow hackers or attackers an opportunity to hack into or infiltrate the organizations network security system.
Wireless pen testing allows access to the consultant into the system who then tries to detect vulnerabilities and exploit them allowing them privileged access to sensitive information.
Thus, wireless pen testing allows the consultants to demonstrate the potential impact of the breach in the wireless network.
- Web Application Penetration Testing
The web application is an integral part and function of the organization. A compromised web application may cause data breaches and leak sensitive information.
Web application penetration testing is a testing method wherein applications on the network are checked for any vulnerabilities or security issues caused by faulty or insecure development, weak design, or improper coding.
- Mobile Application Penetration Testing
Similar to web applications, mobile applications too, is an important arena for an organization. Mobile application penetration testing or security testing is an empowered and simulated hacking attempt against a native mobile application running on devices such as Android, Windows, and iOS.
Mobile application pen testing allows the organization to discover and exploit vulnerabilities in their mobile applications and the way it communicates and transmits data with the back-end systems.
4-Penetration Testing Tools:
- Burp Suite Pro Burp Suite Pro one of the most popular, powerful, and advanced penetration testing tools that can help pentesters to fix and exploit vulnerabilities and identify their target’s more subtle blind spots. It is a “suite” of various advanced tools and, is best suited for penetration testing of web applications.
There are two versions – the community edition offers necessary features such as intercepting browser traffic, managing recon data, and out-of-band capabilities necessary for manual pen testing, while the pro version offers several advanced features such as scanning web application for vulnerabilities. Burp Suite Pro has several features that are incredibly helpful for pentesters, such as the few listed below.
It has a powerful proxy component that performs man-in-the-middle attacks to intercept the transfer of data and lets the user modify the HTTP(S) communication passing through the browser.
Burp Suite helps test out-of-band (OOB) vulnerabilities (those that cannot be detected in a traditional HTTP request-response) during manual testing.
The tool finds hidden target functionalities through an automatic discovery function.
The tool offers faster brute-forcing and fuzzing capabilities which enable pentesters to deploy the custom sequence of HTTP requests that contain payload sets, which drastically reduces the time spent on different tasks.
Burpsuite Pro offers a feature to easily construct a cross-site request forgery (CSRF) Proof of Concept (POC) attack for a given request.
The tool also facilitates deeper manual testing as it can provide a view for reflected or stored inputs.
The app store provides access to hundreds of community-generated plugins which are written and tested by Burp users.
Usage – Best for professionals and expert penetration testers who want to leverage a powerful automated and advanced manual testing tool to uncover critical application-level flaws. Parent company – PortSwigger Platforms – The supported platforms include macOS, Linux, and Windows
- Metasploit Metasploit is a penetration testing framework popularly used by both cyber attackers and ethical hackers. The Metasploit Project has two versions – the open-source sub-project Metasploit Framework and licensed version Metasploit Pro.
Metasploit Framework’s best offering is exploit code and payloads that can be developed and executed against a remote target machine. It provides a command line interface to work on, but testers can also purchase Metasploit Pro for advanced features and GUI-based operations.
Here are a few crucial features of Metasploit:
Metasploit includes more than 1600 exploits that are organised over 25 platforms.
The tool has around 500 payloads that include the following:
Command shell payloads to run scripts against a host.
Dynamic payloads to generate unique payloads to evade antivirus software.
Meterpreter payloads to take control of device monitors, sessions, upload, and download files.
Static payloads for port forwarding and enabling communication between the networks.
Metasploit offer post-exploitation modules which can be used for deep penetration testing. These modules allow pentesters to collect more information about the exploited system such as hashdumps or service enumerators.
Usage – Metasploit is best used where multiple applications or systems are to be tested. Parent company – Rapid7 Platforms – Metasploit is pre-installed in Kali Linux OS. It is also supported on Windows and MacOS.
Budgeting for Penetration Testing
The costing and budgeting depend on several factors and is not constant. The following factors affect the pricing of penetration testing or security testing.
Objective Scope Methodology or Approach: Skills Re-testing
Here are a few common areas that you must focus on when you consider a penetration test:
Network security
Database security
Configuration and identity management
Password vulnerabilities
Check for authentication issues
Vulnerable components
Check for injection vulnerabilities
Cross site scripting attacks
Session handling
Client side protection
Conclusion
In the current global economy, when we hear of cyber-attack instances almost every day, penetration testing has become an indispensable activity for any business that has any form of digital presence.
It is also imperative that pen testing be performed periodically and not be considered as a “one-off” activity. With the growth and scalability of could technology, several start-ups set up operations on a SaaS model.
Being new entrants and relatively young in the business lifecycle, they tend to de-priorities application security.
However, this could prove to be costly as they are lucrative targets for hackers, and one minor incident could result in the business ending even before it started.
Thanks for Reading linkedin.com/in/amrrashad1999